Unveiling Lazarus’ Sophisticated Cryptocurrency Theft Scheme
- blog
- 29/10/2024

A month ago, we wrote a blog post about a new and growing scam targeting blockchain developers. We gave clues as to how to spot this scam, but we didn’t know exactly what it was doing or who it was coming from.
After receiving this scam on an almost daily basis, we investigated a little further and discovered a few things. In particular, the scam was orchestrated by the alleged North Korean group Lazarus.
We now know how this group goes about infecting developers:
Initial Contact: An Offer Too Good to Be True
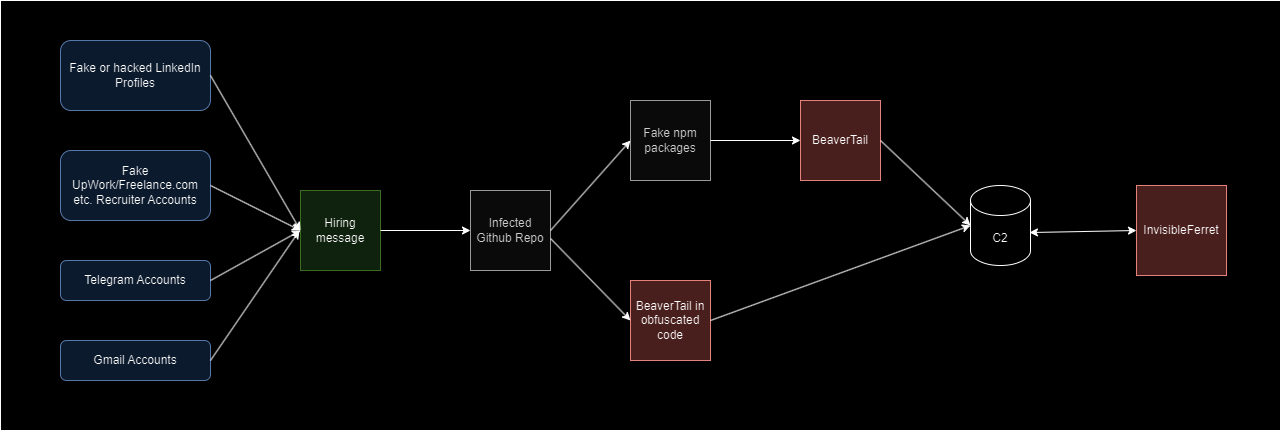
It all began with a message on LinkedIn, on a freelance platform (UpWork, Malt, etc.). A recruiter claiming to represent a blockchain company contacts you with a tempting offer. The promised salary was well above the market average, and the project sounded exciting. After a few exchanges, the recruiter asks for your opinion on his project, sharing the github, gitlab or bitbucket with you.

They can use false names, but also usurp real identities and companies. Sometimes they even buy domain names similar to existing companies to impersonate them.
An infected nodeJS application
The trap is here: you may be asked for your opinion on a current project, or for a technical interview on Google Meet.
What’s the point? Get you to download and compile infected NodeJS code.
At first glance, nothing seems out of the ordinary: the repo is on github (or equivalent), on an account that may have more than 10 years’ activity on real projects.
But on closer inspection, there are fake npm packages or obfuscated code that will take information from browser caches and crypto wallet extensions.
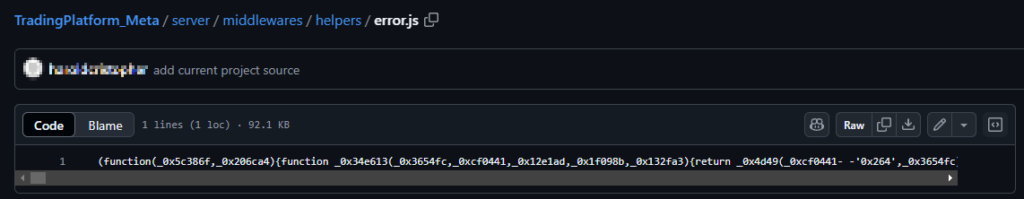
We deobfuscated and analyzed the code. This corresponds to the BeaverTail malware.
This code will first harvest information from browser caches, crypto wallet extensions and some crypto wallet directly like exodus. It will then send this information to a server and download the InvisibleFerret malware, a well-known trojan that enables attackers to retrieve banking information and private keys from cryptowallets.
Here is the list of crypto wallet extensions spied on by BeaverTail that we have identified:
- Metamask
- BNB Chain Wallet
- TronLink
- Phantom
- Coin98 Wallet
- Crypto.com Wallet
- Kaia Wallet
- Rabby Wallet
- Argent X
- OKX Wallet
- Core
- Tonkeeper
- Exodus Web3 Wallet
- Ton Wallet
- OpenMask
- SafePal
- MyTonWallet
- Solflare Wallet
- Atomic Wallet
- Math Wallet
It should also be noted that the code is compatible with Windows, macOS and some Linux distributions.
BeaverTail and InvisibleFerret are still actively under development and their code is evolving month by month.
North Korea behind this scam?
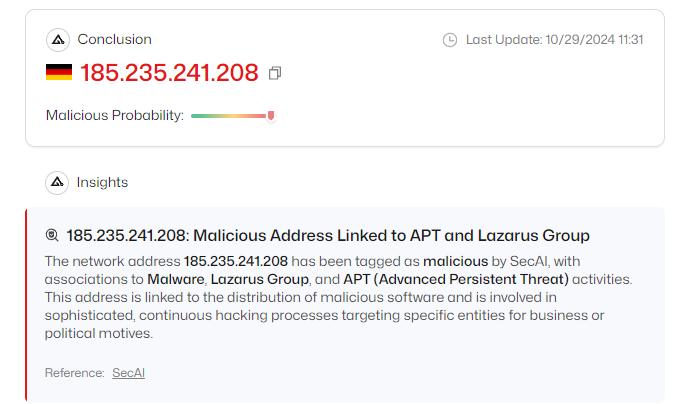
BeaverTail and InvisibleFerret are sophisticated malwares developed by the Lazarus Group, the alleged North Korean hacking collective known for their advanced cybercrime operations. These malwares are part of a larger campaign targeting blockchain developers and freelancers, aiming to steal sensitive information and cryptocurrency. The Lazarus Group’s tactics involve social engineering and phishing to lure unsuspecting victims into downloading and executing malicious code, highlighting the need for vigilance and robust cybersecurity measures.
These scam campaigns have been documented since last year by Unit 42.
Servers that don’t shut down
We have analyzed dozens of Command and Control (C2) servers used by hackers to send malware and receive stolen information.
These servers are hosted in various companies around the world.
One of these companies is Stark Industries Solutions, which Brian Krebs describes as “the epicenter of massive distributed denial-of-service (DDoS) attacks on government and commercial targets in Ukraine and Europe” in his dedicated investigation to this company. He explains that the group NoName057(16) hosts some of these campaigns on Starknet Industries. NoName057(16) is a group of hacktivists known for the Ddosia Project, a botnet that pays individuals to participate in DDOS attacks on Western government agencies.
We solicited Stark Industries, providing them with the evidence they needed to shut down the malicious servers hosted on their premises. To date, we have had no response from them and the servers have been active for over a month.
Conclusion
Hackers are using increasingly sophisticated techniques to deceive their victims. Here are a few recommendations to protect yourself:
- Be Vigilant: Be cautious when recruiters ask you to perform tasks or download applications, especially if these involve executable files.
- Check Companies: Always check that companies and recruiters offering job interviews are genuine and well-established.
- Be Careful with Links: Be careful with links and attachments in unsolicited emails or messages claiming to be from recruiters or companies.
- Use Security Tools: Use up-to-date anti-virus and anti-malware software to scan all files or applications before opening them.
- Always use VMs when running someone else’s code !!
By following these recommendations, you can protect yourself against these sophisticated attacks and stay safe in the digital world.
Many thanks to David Barbier and Corentin Giaufer Saubert who helped us gather the information for this article!